Navigating the Cybersecurity Landscape: Best Practices for Protecting Your Digital Assets
Navigating the Cybersecurity Landscape: Best Practices for Protecting Your Digital Assets
The digital world offers endless opportunities for connection, communication, and innovation. However, this vast online landscape also comes with inherent risks. Cybercriminals are constantly devising new methods to steal data, disrupt operations, and exploit vulnerabilities. To thrive in this environment, it’s crucial to understand cybersecurity best practices and take proactive steps to safeguard your digital assets.

Understanding the Threat Landscape
The first step towards effective defense is understanding the common threats you face. Here are some of the most prevalent cybersecurity threats:
- Malware: Malicious software, including viruses, worms, and ransomware, can infiltrate your devices and steal data, corrupt files, or even render systems unusable.
- Phishing Attacks: Deceptive emails or messages are designed to trick you into revealing sensitive information like passwords or credit card details.
- Social Engineering: Manipulation tactics used to gain your trust and access to sensitive data or systems.
- Hacking: Unauthorized attempts to gain access to computer systems or networks.
- Denial-of-Service (DoS) Attacks: Overwhelming a website or server with traffic to render it unavailable to legitimate users.
Building a Robust Defense: Best Practices for Protecting Your Digital Assets
By implementing the following best practices, you can significantly strengthen your cybersecurity posture:
- Strong Passwords & Multi-Factor Authentication (MFA): Use complex, unique passwords for all your online accounts and enable MFA wherever possible. MFA adds an extra layer of security by requiring a second verification step beyond just your password.
- Software Updates: Always keep your operating systems, applications, and firmware updated with the latest security patches. These updates often address newly discovered vulnerabilities that cybercriminals can exploit.
- Antivirus & Anti-Malware Software: Install reputable antivirus and anti-malware software on your devices and keep them up-to-date. These programs can help detect and block malicious software before it can harm your system.
- Beware of Phishing Attempts: Be cautious of unsolicited emails, messages, or website links, especially those urging immediate action or promising enticing rewards. Don’t click on suspicious links or attachments, and verify the sender’s legitimacy before responding.
- Data Backups: Regularly back up your important data to a secure external drive or cloud storage service. This ensures you have a copy of your data in case of a cyberattack or system failure.
- Secure Wi-Fi Connections: Avoid using public Wi-Fi networks for sensitive activities like online banking. If you must use public Wi-Fi, consider using a Virtual Private Network (VPN) to encrypt your internet traffic.
- Social Media Awareness: Be mindful of what information you share on social media platforms. Cybercriminals can use this information to target you with social engineering attacks.
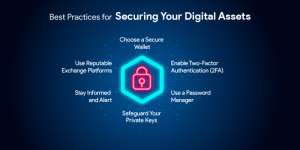
Beyond the Basics: Building a Culture of Cybersecurity
Effective cybersecurity goes beyond individual actions. Here’s how to cultivate a culture of cybersecurity within your organization or household:
- Security Awareness Training: Educate everyone about cybersecurity threats and best practices. Regular training helps everyone stay informed and vigilant.
- Clear Security Policies: Establish clear and comprehensive security policies that outline acceptable online behavior and data handling practices.
- Incident Response Plan: Develop a plan for addressing cyberattacks if they occur. This plan should outline steps for containing the incident, mitigating damage, and recovering data.
By following these best practices and fostering a culture of cybersecurity awareness, you can significantly reduce the risk of falling victim to cyberattacks and safeguard your valuable digital assets. Remember, cybersecurity is an ongoing process, so it’s important to stay informed about evolving threats and adapt your defenses accordingly.
Conclusion:
In today’s digital landscape, a robust cybersecurity posture is no longer a luxury, but a critical business imperative. By implementing the best practices outlined in this guide, you can significantly strengthen your defenses, safeguard sensitive data, and minimize the potential for costly cyberattacks. Remember, the threat landscape is constantly evolving, and remaining vigilant and proactive is key to staying ahead of emerging threats.
Confidently navigate the ever-evolving cloud security landscape with the power of CloudFence.ai.
Our comprehensive platform provides the essential tools and insights to:
- Prioritize Cybersecurity: Establish our dedicated cybersecurity team or appoint a cybersecurity champion to spearhead the implementation of best practices.
- Conduct a Security Assessment: Identify vulnerabilities within your systems and networks through our penetration testing and vulnerability scanning.
- Invest in Security Solutions: Implement robust security software, firewalls, and encryption tools to protect your data and systems.
- Educate Your Employees: Regularly train employees on cybersecurity awareness and best practices to foster a culture of security within the organization.
- Develop a Response Plan: Create a comprehensive incident response plan to effectively address and mitigate potential cyberattacks.
- Seek Expert Guidance: Partner with a cybersecurity professional for tailored recommendations and ongoing support in building a secure digital environment.
About CloudFence.ai
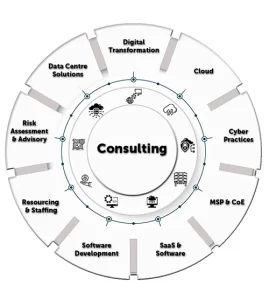 CloudFence Technologies leads the way in cutting-edge Technology Consulting, offering unmatched Cloud Services, SaaS, Risk & Cyber, and Digital Transformation Solutions globally. We are dedicated to providing you with the flexibility to seamlessly transition, construct, and optimize applications across hybrid and multi-cloud environments. This approach reduces vendor lock-in, allowing us to harness top-notch solutions that adhere to regulatory requirements. Collaborating with a diverse range of Technology firms, Clients, OEMs, ISVs, Consumer Internet, and large enterprises worldwide, we consistently surpass expectations. Identifying organizational gaps, we navigate through dual criteria to meet urgent short-term targets for immediate results while simultaneously developing the essential competencies needed to realize the long-term vision.
CloudFence Technologies leads the way in cutting-edge Technology Consulting, offering unmatched Cloud Services, SaaS, Risk & Cyber, and Digital Transformation Solutions globally. We are dedicated to providing you with the flexibility to seamlessly transition, construct, and optimize applications across hybrid and multi-cloud environments. This approach reduces vendor lock-in, allowing us to harness top-notch solutions that adhere to regulatory requirements. Collaborating with a diverse range of Technology firms, Clients, OEMs, ISVs, Consumer Internet, and large enterprises worldwide, we consistently surpass expectations. Identifying organizational gaps, we navigate through dual criteria to meet urgent short-term targets for immediate results while simultaneously developing the essential competencies needed to realize the long-term vision.
“As your strategic partner, CloudFence Technologies is committed to driving innovation and ensuring your business stays ahead in the dynamic landscape of technology. Trust us to not only meet your current needs but also to anticipate and navigate the evolving challenges of tomorrow, guiding you towards sustained success in the ever-evolving digital realm.”