MITRE ATT&CK, Attack Flow, M3TID: Unpacking the CTID Toolbox, 2023-24 & Beyond
MITRE ATT&CK, Attack Flow, M3TID: Unpacking the CTID Toolbox, 2023-24 & Beyond
Imagine you’re a homeowner battling burglars. The old way was to just lock your doors and hope for the best. But now, there’s a smarter approach called “crime-informed defense.” This means learning how burglars operate, their preferred tricks and tools, and then using that knowledge to fortify your home in smart ways, Lets use this information to understand how CTID functions.
The Center for Threat-Informed Defense (CTID) is like a neighborhood watch for cybersecurity. They gather information about cybercriminals (the “burglars” of the digital world), their tactics (breaking windows, climbing ladders), and their tools (crowbars, lockpicks). Then, they share this knowledge with everyone through tools and resources like:
- Attack Flow: Think of it as a video camera that catches how burglars move through a house, showing all the steps they take. This helps homeowners visualize how attacks unfold and identify weak spots.
- Technique Inference Engine: Like a fortune teller, it uses clues from past burglaries to predict what the next move might be, helping homeowners prepare before it happens.
- CTI Blueprints: Imagine police report templates for burglaries. These guides help security teams write clear and concise reports about cyberattacks, making it easier to share information and learn from each other.
- Adversary Emulation Library: This is like a practice gym for security teams. It provides simulated burglaries with different scenarios, so teams can test their defenses and find vulnerabilities before real attackers strike.
- Summiting the Pyramid: Picture a pyramid where the bottom is easy for burglars to bypass and the top is almost impossible. This framework helps security teams build defenses that climb higher on the pyramid, making it harder and harder for attackers to succeed.
By sharing this knowledge and tools, CTID empowers businesses and organizations to become smarter defenders against cyber threats. They’re basically helping everyone build stronger digital homes and making the online world a safer place for everyone.
In this revision of our 2023 Research and Development (R&D) Roadmap, we will showcase significant contributions from the Center in each domain, emphasizing noteworthy achievements. The concluding segment of this update will provide insights into our ongoing initiatives and explore emerging research areas.
Technological Advancements in CTID: The Way Forward
MITRE ATT&CK®: Measuring Defensive Posture:
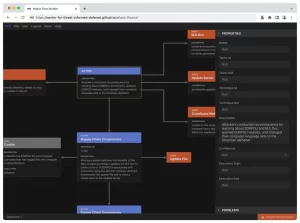
MITRE ATT&CK® serves as a pivotal tool in evaluating defensive postures, offering distinct elements for analysis. Beyond static defense, understanding how adversaries sequence techniques is crucial. The CTID has responded to this by developing the Attack Flow, a data model representing the sequence of adversary behaviors. This model, presented through a web application, allows users to construct and visualize attack flows, forming the foundation for discussions surrounding the entire threat-informed defense lifecycle.
Attack Flow Builder
-
Collaborative Incident Response:
- The Attack Flow Builder serves as a catalyst for seamless collaboration among security teams.
- Incident response teams can efficiently document attack scenarios, initiating a streamlined process that fosters collaboration between various security units.
-
Information Sharing with Intel Teams:
- One of the key functionalities is the sharing of documented attack flows with intelligence teams.
- Intel teams benefit from a comprehensive visual representation of attack sequences, enabling them to gain valuable insights into adversary tactics.
-
Integration into Reporting:
- The Attack Flow Builder seamlessly integrates documented attack flows into comprehensive security reports.
- This integration extends to the entire security organization, ensuring that insights derived from attack flows become a crucial component of collective defense strategies.
-
Enhancements for Accessibility:
- Recognizing the importance of use case documentation, ongoing efforts are dedicated to further enhancing the accessibility of the Attack Flow Builder.
- Future updates will focus on user-friendly features to streamline the process of documenting use cases, making it even more accessible for security professionals.
The Attack Flow Builder stands as a practical tool not only for incident response but also for cultivating a collaborative and informed security environment. The continuous improvements aim to empower security teams in their efforts to understand, respond to, and mitigate cyber threats effectively.
Technique Inference Engine (TIE):
Launching this month, TIE aims to predict unobserved behavior based on a given sequence of observed techniques. Leveraging data from a cadre of committed participants, the project analyzes techniques and sequences, allowing for the inference of the adversary’s next move with a measurable degree of certainty.
Empowering CTI Teams: The backbone role of CTI reporting

Upgraded CTI Resources:
In 2023, the Center enhanced the ATT&CK Workbench, enabling teams to customize and extend ATT&CK for their unique needs. The new Workbench allows organizations to host instances, serving as the centerpiece for their customized ATT&CK knowledge base. Additionally, the 2023 release of TRAM showcases the ability of Large Language Models to automate technique detection in threat intelligence reports.
CTI Blueprints:
Recognizing the backbone role of CTI reporting, the Center introduced CTI Blueprints. These templates, developed by leading intelligence consumers, offer a resource for high-quality, less manually-intensive reporting. They include customizable sample reports and an open-source suite of authoring and publishing tools.
Adversary Emulation Library: Expanding Coverage
- The Adversary Emulation Library, initially designed with a focus on Windows, has undergone significant expansion to address the evolving threat landscape.
- Recognizing the prevalence of threats targeting Mac and Linux systems, the Library now includes emulation plans for these platforms.
- Beyond the traditional emphasis on full-scope breach scenarios, the Library has introduced six additional plans, each tailored to target specific behaviors and challenges frequently encountered by defenders.
Summiting the Pyramid of Pain: Enhancing Detection Engineering
- The Summiting the Pyramid project is a strategic initiative aimed at confronting the challenges associated with adversaries easily evading common detection measures.
- Introducing a systematic framework, this project enables the evaluation and elevation of detections up the Pyramid of Pain, ultimately making it more arduous for adversaries to evade detection.
- By addressing the limitations observed in many existing detections, the project seeks to enhance the effectiveness of analytics in identifying and responding to cyber threats.
Sensor Mappings and Integration: Comprehensive Security Views
- n December 2023, the Center is scheduled to release Sensor Mappings to ATT&CK, providing security professionals with a holistic view of observables sourced from common logs, sensors, and various defensive capabilities.
- The ongoing efforts in mapping native security controls in M365 to adversary techniques are set to be unveiled in March 2024, further enriching the understanding of how adversaries leverage different techniques against Microsoft’s cloud services.
- This project aims to standardize mappings in a single data format, promoting usability and future growth, allowing defenders to explore mapped security controls from the perspective of the ATT&CK techniques they mitigate.
Active Research and Future Projects

M3TID Project:
The Measure, Maximize, and Mature Threat-Informed Defense (M3TID) project seeks to establish a measurement standard for defensive posture. It encourages community collaboration to define best practices for coverage against Tactics, Techniques, and Procedures (TTPs).
Secure AI Focus Area:
Collaborating with MITRE ATLAS™, CTID’s Secure AI focus area explores threats against AI systems. Building on the success of applying threat-informed defense to OT systems, threat modeling, and insider threats, the Center aims to red team AI systems and develop mitigations.
Global Engagement and Initiatives
Benefactor Program:
CTID invites organizations to support its research through the Benefactor Program. Contributions from organizations like Coalfire and Acalvio Technologies enable the Center to scale its impact.
Asia-Pacific ATT&CK Community Workshop:
In 2024, the Center extends its community engagement by hosting the first Asia-Pacific ATT&CK Community Workshop in Singapore. Threat-informed defenders in the region are encouraged to participate in this inaugural event.
Ready to amplify your threat-informed defenses with intelligent security? Cloudfence.ai offers robust solutions that complement your CTID initiatives:
Uncover hidden threats with unparalleled insights:
- Gather and analyze vast amounts of threat intelligence using Cloudfence.ai’s network, staying ahead of emerging threats and attacker tactics.
- Detect malicious activity with exceptional accuracy through AI-powered detection models, stopping attacks before they cause damage.
- Learn more about Cloudfence.ai’s intelligent security solutions: [https://www.cloudfence.ai/edr-xdr-as-a-service]
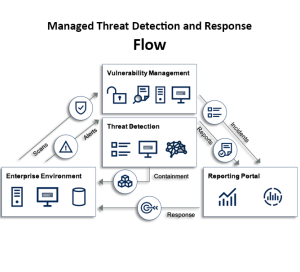
Conclusion:
The Center’s commitment to advancing global threat-informed defense is evident in its diverse projects and initiatives. As it enters its fifth year, the Center remains dedicated to collaborative efforts with the community, fostering engagement and evolving its work to meet the ever-changing challenges posed by cyber adversaries.
Get Involved:
The Center encourages community support and engagement to further its mission. Stay informed, utilize CTID R&D resources, and provide feedback to contribute to ongoing improvements. For organizations seeking active participation, becoming a Center Participant offers a unique opportunity to collaborate in a uniquely supportive environment. Click here for CTID R&D resources.

